Due to its strong reliance on digital data files and connectivity, AM by nature is subject to significant security exposures, from product malfunctions to intellectual property theft and brand risk, along with other new threats users of conventional manufacturing processes do not usually face. If acknowledging this reality is a business imperative, there is still a gap between assessing the potential impact of AM-specific cybersecurity concerns and what can be done about that.
Last year, analysts at Gartner forecast that 43 billion IoT-connected devices will be leveraged across the world. In the manufacturing industry alone and according to independent research analyst Jannik Lindner, 47% of manufacturers have experienced cyber-attacks on their Industrial Internet of Things (IIoT) devices. Speaking of the AM industry especially, Lindner continues: about “54% of manufacturers across the world do not monitor their systems for suspicious behavior.” Yet, “60% of manufacturers reported suffering a disruptive cyberattack within the past 24 months.”
I strongly believe that if these AM industry statistics are alarming, that’s probably because companies deploying AM technologies consider addressing this issue an overwhelming task.
Different scenarios where AM-specific cybersecurity concerns may arise
One of the most mentioned AM-specific cybersecurity concerns is the case of design files that can be stolen. Other AM-specific cybersecurity concerns include the fact that design files can be changed to create flaws in parts, the toolpath can be modified to deposit materials incorrectly, dangerous or illegal parts or objects can be printed, digital twin or digital thread can be hacked, thus compromising maintenance or quality control.
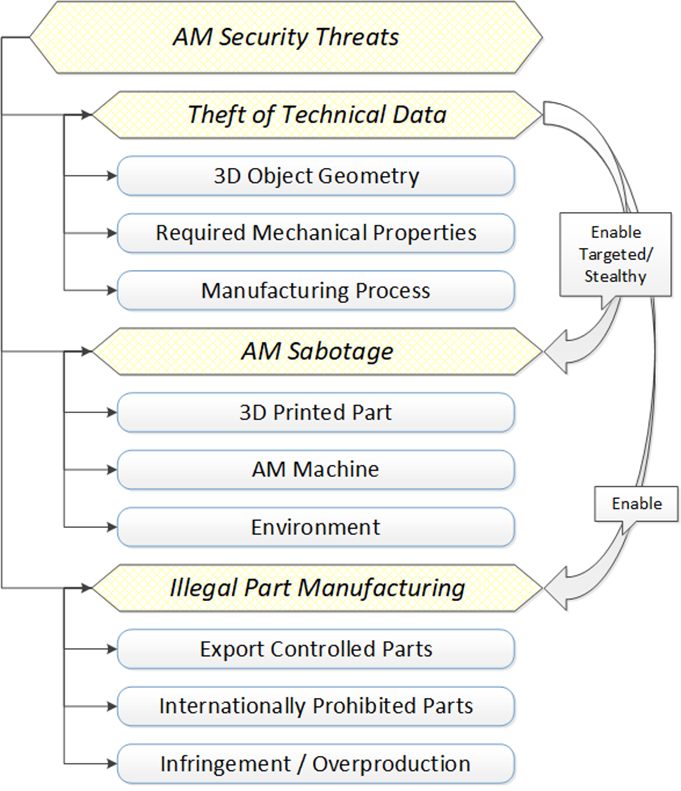
Mark Yampolskiy, an Associate Professor of Computer Science and Software Engineering at Auburn University, summarizes these threats into three main categories.
“The first one is Technical Data Theft (TDT), which is commonly discussed in the context of Intellectual Property (IP) protection. However, not all data whose loss the defender would like to prevent is or can be protected as IP. Furthermore, there are kinds of data that a defender might consider negligible, but that can advance the attacker’s goals.
The second one is Sabotage, which is sometimes discussed in the context of integrity violation. However, not all integrity violations will lead to sabotage, and there are means to achieve sabotage without violating the classical integrity of cyber items, such as digital designs. In AM, sabotage can be directed immediately against the manufactured part or the machine. However, indirectly and more importantly, it can affect the system in which such part is integrated, or the environment of the AM machine.
The third is the use of AM for Illegal or Unauthorised Part Manufacturing (IPM). This is a threat distinct from the first two, because AM machines do not prevent manufacturing anything that is physically possible. Therefore, it is rather a legal concern for which a technical solution is sought.
Lastly, as AM Security is still a young discipline, it is likely that new threats will emerge. For example, we recently discovered that it is possible to embed additional information in the STL design file without affecting the design or printed part (using something known as ‘steganographic channels’). This threat does not aim at AM, but rather uses AM as an ‘accessory’ to further other attacks.
There are also ‘symbiotic relationships’ between threats. For example, TDT can be a precursor for a targeted sabotage attack (e.g., to design a defect for a specific part that will degrade its functional characteristics to a certain degree) or for IPM (e.g., to infringe parts using a stolen design). The steganographic channels in STL (and probably in other digital file formats used in AM) can be used to exfiltrate the stolen data ‘piggybacking’ on innocuous-looking design files sent outside a company or an organization.”
Potential impacts that may arise therefore include financial fraud, reputation damage or theft of IP, business disruption, destruction of critical infrastructure, threats to safety or even regulatory infringement.
So, how do you map these cybersecurity risks across the AM lifecycle?
As seen above, cybersecurity threats can occur at different levels. Therefore, it’s crucial to understand how data are transmitted and processed – and how information is communicated throughout the AM process, from design, build, and quality assurance monitoring, to testing, delivery, and distribution. Understanding that process comes down to establishing the digital thread specific to your organization and most importantly, identifying the stakeholder that could be impacted the most.
That stakeholder could be the AM equipment manufacturer, the 3D part designer, the material supplier, or the end customer.
Defining which stakeholder is impacted the most by a security threat in an AM workflow “depends on the threat we are talking about”, Yampolskiy outlines before adding: “original equipment manufacturers (OEM) and 3D part designers are probably the most affected by TDT. Their concerns might be different, though. The OEM is likely to be mostly concerned with their ‘secret sauce’, such as scanning strategy and process parameters for a specific material. The 3D part designers are likely to be more concerned about their design being stolen and infringed upon.
End customers are more affected if we talk about sabotage of parts. Having said that, an attack on the material supplier can be used to sabotage the feedstock to sabotage parts manufactured with it – a physical equivalent of what is known in cybersecurity as a ‘supply chain attack’.”
What steps can be taken to address AM cybersecurity threats?
First and foremost, it’s crucial to keep in mind that cybersecurity is not just an IT department issue. Therefore, everyone in the organization should be aware of the risks and ensure basic precautions are followed to prioritize safety.
If there is a scenario where we can’t address all the security challenges at the same time, defining the most important hurdle to address can be “a tough choice because different stakeholders might be more or less exposed to different threats. And this might change over time. Just two years ago I would answer the question by pointing at TDT. However, considering the current global instability and the return of great powers competition, I would say that Sabotage should be our main concern, at least for the time being”, the associate professor points out.
That being said, it’s never a bad idea to first conduct a thorough risk assessment to pinpoint the risks most pertinent to one’s specific AM scenario. This could also help pinpoint potential additional threats that might come into play with regard to AM applications.
One could also assess if lessons from well-known cyber-attacks could be applied to AM. According to a report from Deloitte on “3D opportunity and cyber risk management”, the “strategy, “test once, satisfy many,” can enable organizations to consider the applicable regulations in the same vein to avoid duplicating efforts, particularly when used in concert with design approaches that incorporate security directly into the design of products. They can then create a comprehensive risk management framework to evaluate their regulatory environment to best address their specific cybersecurity footprint. Given the fact that AM processes include both digital and physical components, a combination of strategies focused on both IT systems and physical objects may provide the most comprehensive initial approach.”
Furthermore, since the manufacturing process chain starts with the design – and given the fact that it is often the first cybersecurity risk considered, a part of the basic precautions can be the protection of one’s design from the start. Together with his partners for example – they include Dr. Moti Yung (Google LLC, Columbia University), Dr. Nikhil Gupta (New York University), and Hammond Pearce (University of New South Wales) –, Yampolskiy has been developing a “solution for integrating robust digital watermark into STL design files.”
Another step could consist in ensuring protection into one’s print process. Security solutions that could be implemented, depend on many factors including the type of AM technologies used, or even the standards one can afford to pay. For example, Velo3D printers can be configured to meet the rigorous security requirements of the United States Department of Defense (DoD). To do so, their users should achieve the Security Technical Implementation Guides (STIGs) compliance developed by the Defense Information Systems Agency (DISA). According to OEM Velo3D, “in the realm of metal AM, the application of STIGs is particularly crucial due to the unique challenges and vulnerabilities inherent in this field. The technology involves complex processes that integrate digital designs, advanced materials, and precision engineering. Each of these components introduces specific security risks that STIGs are designed to mitigate. For instance, the digital design files used in metal AM are highly sensitive. If compromised, they could lead to significant intellectual property theft and national security threats. STIGs provide comprehensive guidelines to secure these digital assets, ensuring that they are stored, transmitted, and accessed in a manner that minimizes the risk of unauthorized access or tampering.”
Other practices are seen in tracking and tracing. They include the use of RFID tags to track AM-produced products throughout the supply chain.
Speaking of a non-invasive solution that could be used to detect sabotage attacks, Yampolskiy explains they “use what is known as ‘side channels’, focusing on the power side channels of individual actuators. The approach has several advantages compared to pure cybersecurity solutions. To name just one, such an approach allows to air-gap the monitoring system from the monitored 3D printer, thus significantly increasing the difficulty of their simultaneous compromise. The project for the adoption of this approach to PBF is funded by NIST.”
Concluding thoughts?
Improved cyber protection will give manufacturers and their customers the confidence to try new business practices and models they can’t consider now. The potential for new opportunities supported by cybersecurity will draw in innovative companies with cybersecurity expertise to provide solutions for Additive Manufacturing users and AM technologies providers. While we look forward to sharing cybersecurity solutions applied across business models such as remote manufacturing, and/or on-demand spare parts production, one should keep in mind that cybersecurity threats ultimately drive change and growth – especially when tackled creatively.
This dossier has first been published in the May/June edition of 3D ADEPT Mag.






